This set of Cognitive Radio written test Questions & Answers focuses on “Next Generation Wireless Network – Cognition Policy Engine – 2”.
1. Which among the following functions is not supported by the Ponder policy management framework?
a) Administration of domain hierarchies
b) Positive authorization
c) Negative authorization
d) Memory optimization
View Answer
Explanation: The ponder policy management framework consists of a policy language with a set of tools and source code available freely on the internet. The tools can administrate domain hierarchies, allow positive and negative authorization policies, delegate policies, and support event-triggered condition-action rules.
2. Which among the following policies is associated with event-triggered condition-action rules?
a) Obligation policies
b) Authorization policies
c) Assignment policies
d) Acknowledgment policies
View Answer
Explanation: The Ponder language is regarded as a declarative, object-oriented language that can define obligation and authorization policies. Obligation policies are event-triggered condition-action rules that can be used to describe adaptable management actions. Authorization policies are used to define the set of resources available for each user access.
3. Which among the following is a unique feature of Ponder language?
a) Analysis
b) Authorization
c) Priority assignment
d) Memory optimization
View Answer
Explanation: Policy language allows assignment of priorities and preference. Priority assignment aids in the resolution of conflicts as the sequence of execution is clearly defined. It allows the prioritization of rules to reflect local management priorities. For example, a rule can ensure that efficiency is given more importance than reliability.
4. Which among the following plays the role of a policy decision point in KAoS?
a) Priority manager
b) Spectrum broker
c) Domain manager
d) Resource administrator
View Answer
Explanation: KAoS is a semantic web language and is used to enforce policies in terms of software context. The domain manager operates as the policy decision point and interprets policies to control the behaviour of the network. It administers policies ranging over all domains.
5. Which among the following can be observed as a result of hierarchical policy management?
a) Extension of policy decision point beyond linear order of priorities
b) Introduction of rigidity between groups
c) Higher degree of abstraction
d) Easy access between management units
View Answer
Explanation: Hierarchical policy management and domain groupings introduce additional flexibility by allowing a policy decision point to extend beyond the linear ordering of priorities. In the inheritance hierarchy, policies created from the local domain have higher priority in the device.
6. Which among the following is the function of meta-policies?
a) Resource allocation
b) Administration of layer-specific application hierarchies
c) Administration of domain hierarchies
d) Handle non-linear priorities
View Answer
Explanation: Metapolicies can aid policy decision point in handling nonlinear priorities, solving conflicts, and ambiguities between overlapping rules. Metapolicies constrain the interpretation of groups of policies. For example, language can permit the addition of domain-specific information without modification.
7. Which among the following is the expansion PCIM framework?
a) Priority Core Infrastructure Model
b) Policy Core Infrastructure Model
c) Policy Core Information Model
d) Priority Core Information Model
View Answer
Explanation: Policy Core Information Model initiated the process of standardizing policy management terminology. It represents network management policies. The framework can support vendor-specific implementations.
8. Which among the following is not a primary goal of network access part of the cognitive policy engine?
a) Promote manual control of networks
b) Develop machine-readable policies
c) Security
d) Network application performance
View Answer
Explanation: Network policy management involves the creation of policy enabled devices that are capable of enforcing policies. The administrators use policy languages to represent network objectives. Policy servers configure the device to accomplish the objectives. Security, optimization of the performance of network applications, automating the control of networks, and the development of machine-readable policies are the primary objectives.
9. In common open policy service, the provisional models store all policies at the policy decision point.
a) True
b) False
View Answer
Explanation: Common open policy service has two models namely the outsourcing model and the provisional model. In the outsourcing model, the policy decision point holds all policies. In the provisional model, only the policies requested by the policy enforcement point are downloaded.
10. Which among the following options should replace the labels ‘A’, ‘B’, and ‘C’?
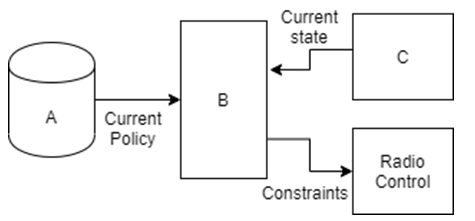
a) Status monitor, Policy engine, Policy database
b) Policy database, Policy engine, Status monitor
c) Status monitor, Policy database, Policy engine
d) Policy engine, Policy database, Status monitor
View Answer
Explanation: The policy engine interprets and enforces spectrum policies. Additionally, it overlooks platform events to provoke alteration in the radio function. The interface between the policy engine and radio platform represents the controlling and monitoring functions of the radio.
Sanfoundry Global Education & Learning Series – Cognitive Radio.
To practice all written questions on Cognitive Radio, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
