This set of Cognitive Radio online test focuses on “Next Generation Wireless Network – Upper Layer Issue – 2”.
1. Which among the following does not cause performance degradation on TCP level?
a) Link error
b) Packet loss
c) Admission control
d) Access delay
View Answer
Explanation: Transmission Control Protocol is a connection oriented, reliable, end to end protocol of the transport layer. TCP generally exhibits performance degradation in wireless networks due to a high packet loss rate. Cognitive radio introduces new challenges such as interruption due to loss of availability of a channel.
2. Which among the following influences packet loss probability?
a) Operation frequency
b) Interference level
c) Available bandwidth
d) Medium Access Control protocol
View Answer
Explanation: Packet loss probability is computed to predict wireless link error. It relies on the access technology, operating frequency, interference level, and available bandwidth. Wireless channel access delay relies on operation frequency, interference level, and medium access control protocol.
3. Which among the following factors influence round trip time?
a) Access technology
b) Power efficiency
c) Cost
d) Frequency of operation
View Answer
Explanation: Round trip time depends on the frequency of operation. An increased number of link layer retransmissions is required to send a packet across the wireless channel when a high packet error rate is observed at a particular frequency band.
4. What is spectrum handoff latency?
a) Spectrum handoff latency is the time taken to switch to a new frequency during handoff
b) Spectrum handoff latency is the period over which an xG user can use licensed band before handoff
c) Spectrum handoff latency is the time taken to estimate the path between a current licensed band and a new licensed band
d) Spectrum handoff latency is the time taken to send handoff information to the spectrum broker
View Answer
Explanation: Depending on the available spectrum, the operational frequency of the radio changes with time. When the radio changes its frequency of operation, the time taken for the new frequency to become operational is called spectrum handoff.
5. Which among the following increases with an increase in spectrum handoff latency?
a) Overhead
b) Time of arrival
c) Round trip time
d) Link layer delay
View Answer
Explanation: High spectrum handoff latency leads to increased round trip time. This in turn leads to retransmission time out. Existing protocols deduce the cause as packet loss and invoke the congestion avoidance mechanism resulting in the decrease of throughput. Cognitive radio network requires transport protocols that support spectrum mobility.
6. Which among the following is the first step in multipath routing?
a) Selection of a spectrum band for transmission
b) Identification of multi-paths
c) Evaluation of route metrics
d) Selection of route metrics
View Answer
Explanation: In multipath routing, the multiple paths are discovered first. The routes are evaluated on route metrics such as delay and link stability, and then the node selects a route for transmission. One approach is to employ dynamic source routing for route discovery. Multipath routing suits the dynamic nature of cognitive networks and exhibits increased efficiency.
7. Which among the following is true about tree based routing?
a) Tree based routing is a distributed routing scheme controlled by a multiple network entities
b) Tree based routing is a distributed routing scheme controlled by a single network entity
c) Tree based routing is a centralized routing scheme controlled by a single network entity
d) Tree based routing is a centralized routing scheme controlled by a multiple network entities
View Answer
Explanation: Tree based routing is a centralized network scheme controlled by a single network entity. xG users register at the centralized entity. One approach is to construct a route based on end to end throughput at the centralized entity using the minimum spanning tree algorithm.
8. Which unit is responsible for initiating local coordination?
a) Primary user
b) Secondary user
c) Central entity
d) Intermediary node
View Answer
Explanation: Local coordination routing is a combination of routing and spectrum assignment protocol, and local coordination scheme. The routing and spectrum assignment protocol generates multiple paths and assigns a cost for each hop in the path. The intermediary nodes initiate local coordination and find alternate paths to tackle link failure.
9. Which among the following occurs when intermediary nodes choose identical frequency bands?
a) Link failure
b) Increased cost
c) Increased power
d) Increased delay
View Answer
Explanation: In the location coordination scheme, multihop paths are created, where intermediary nodes might select an identical frequency band. It results in increased switching delay. This can be avoided by introducing a scheduling mechanism such as polling.
10. Which among the following statements is false about spectrum aware routing?
a) Spectrum aware routing does not require local spectrum knowledge
b) Spectrum aware routing requires cooperation sensing
c) Spectrum aware routing performs poorly during link failure
d) Spectrum aware routing does not generate large overhead
View Answer
Explanation: Spectrum aware routing operates with global knowledge as well as with local knowledge. Each user is aware of another user when global knowledge is available. Otherwise each user constructs spectrum routes using spectrum availability information obtained locally by distributed protocol.
11. Which layer is associated with based utility attack?
a) Physical layer
b) Data link layer
c) Network layer
d) Transport layer
View Answer
Explanation: Based utility attack involves the modification of characteristics of function parameters to obtain more bandwidth. It increases the amount of delay in the network. It is observed in the data link layer.
12. A key depletion attack is a malicious attack on the network layer.
a) True
b) False
View Answer
Explanation: The key depletion attack is a malicious attack on the transport layer. It is employed to destruct the underlying cipher system. It leads to the degradation of the efficiency of communication.
13. What type of mechanism is exhibited in the following diagram?
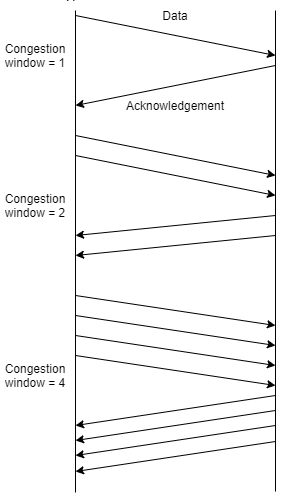
a) Slow start
b) Three way handshake mechanism
c) Fast retransmission
d) Selective retransmission
View Answer
Explanation: The slow start mechanism involves starting the communication with a minimum number of packets. On receiving an acknowledgment, the amount of packets is doubled. This is continued until the number the packets reach the receiver’s buffer limit or until congestion is detected.
Sanfoundry Global Education & Learning Series – Cognitive Radio.
To practice all areas of Cognitive Radio for online tests, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
