This set of Cognitive Radio Multiple Choice Questions & Answers (MCQs) focuses on “Next Generation Wireless Network – Spectrum Sharing – 1”
1. Which among the following is not used as an attribute for classifying spectrum sharing?
a) Architecture
b) Spectrum allocation behaviour
c) Spectrum access technique
d) Spectrum sensing behaviour
View Answer
Explanation: Based on the architecture, the spectrum sharing techniques are categorized as centralized and decentralized. Based on spectrum allocation behaviour, the techniques are categorized as cooperative and non-cooperative. Based on the spectrum access technique, the methods are categorized as overlay and underlay.
2. Which among the following statement is false about cooperative sensing?
a) Cooperative spectrum sharing is alternately known as collaborative spectrum sharing
b) Cooperative spectrum sharing studies the effect of communication of one node on other nodes
c) Cooperative spectrum sharing withholds the interference information
d) Cooperative spectrum sharing minimizes collision caused by users accessing the same portion of the spectrum
View Answer
Explanation: Cooperative spectrum sharing studies the effect of communication of one node on other nodes. It also involves distributing the interference measurements among the users in the network. This information is utilized by spectrum allocation algorithms which provide spectrum access to users.
3. Which among the following is true non-cooperative spectrum sharing?
a) Non-cooperative spectrum sharing optimizes spectrum sharing algorithms
b) Non-cooperative spectrum sharing reduces effective spectrum utilization
c) Non-cooperative spectrum sharing distributes interference measurements to other users in the network
d) Non-cooperative spectrum sharing works only with spectrum broker
View Answer
Explanation: Non-cooperative spectrum sharing only considers the communication of the one particular node. Due to the lack of information about other users, it exhibits reduced spectrum utilization. However due to minimal communication requirements, it is suitable for certain resource-constrained practical applications.
4. What is the parameter used to differentiate the overlay and underlay spectrum sharing technique?
a) Delay in unlicensed spectrum
b) Delay in licensed spectrum
c) Degree of interference exhibited towards primary user
d) Degree of interference exhibited towards secondary user
View Answer
Explanation: The overlay and underlay spectrum sharing techniques are classified based on the amount of interference directed towards the primary users while operating in the licensed spectrum band. Overlay exhibits zero interference while the underlay technique exhibits considerable interference which is regarded as noise by primary users.
5. Which among the following method is employed in underlay spectrum sharing?
a) Time division multiple access
b) Spread spectrum techniques
c) Frequency division multiple access
d) Time division duplexing
View Answer
Explanation: Underlay spectrum sharing technique employs spread spectrum techniques while transmitting in the licensed portion of the spectrum band. Spread spectrum involves stretching a signal over a bandwidth which is wider than its original bandwidth. Therefore bandwidth utilization and interference towards the primary user is increased.
6. Which among the following is true about centralized spectrum sharing?
a) Centralized spectrum sharing does not rely on fixed infrastructure units
b) Centralized spectrum sharing holds each node responsible for spectrum allocation
c) Centralized spectrum sharing reduces the overhead of communication
d) Centralized spectrum sharing has a controlling entity for spectrum allocation and spectrum access
View Answer
Explanation: Centralised spectrum sharing consists of a central entity for performing spectrum allocation and spectrum access. Each node in the network forwards information on the spectrum and the interference to the central entity. The central entity builds the spectrum allocation map using the collected information.
7. Which among the following has to be carried out after the spectrum is allocated for communication?
a) Listen for the arrival of the primary user
b) Handshake mechanism between transmitter and receiver
c) Estimate the duration of communication
d) Forward interference information to spectrum broker
View Answer
Explanation: The selected portion of the spectrum must be informed to the receiver of data. This is accomplished by invoking a transmitter-receiver handshake protocol that is used for effective communication in xG networks.
8. Which among the following is not a step in spectrum sharing?
a) Spectrum sensing
b) Spectrum mobility
c) Spectrum access
d) Spectrum management
View Answer
Explanation: Spectrum sharing process is integrated with spectrum sensing, spectrum allocation, spectrum access, handshake mechanism, and spectrum mobility. Thus the selection of best available spectrum, prevention of collision due to the overlapping portion of the spectrum, and seamless connection for communication regardless of the location of the user involves spectrum sharing.
9. Which among the following layer operation is similar to that of spectrum sharing?
a) Physical
b) Data-link
c) Network
d) Transport
View Answer
Explanation: The data link layer particularly the MAC portion is responsible for collision avoidance. Likewise, spectrum sharing is responsible for avoiding collision between licensed and unlicensed users of the licensed spectrum band as well as for avoiding collision among xG users in the unlicensed band.
10. Which among the following is a constraint observed in hardware constrained MAC protocol for cognitive radio networks?
a) Hidden terminal problem
b) Synchronization among xG users
c) Synchronization between xG user and primary user
d) Shadowing uncertainty
View Answer
Explanation: Sensing in a limited geographic area with a fixed bandwidth limit on secondary users is a challenge for hardware constrained MAC protocol. Thus hidden terminal problem is observed in the hardware constrained MAC protocol. The demand for synchronization among xG users is a problem of concern for cognitive MAC protocol.
11. Transmitter-receiver handshake does not involve any central entity such as the primary base-station.
a) True
b) False
View Answer
Explanation: The transmitter-receiver handshake conveys the selected spectrum for communication to the receiver. This protocol is not limited between a transmitter and a receiver and may also include external entities such as a primary base-station especially in methods such as cooperative spectrum sharing.
12. Which among the following terms should replace the label ‘A’?
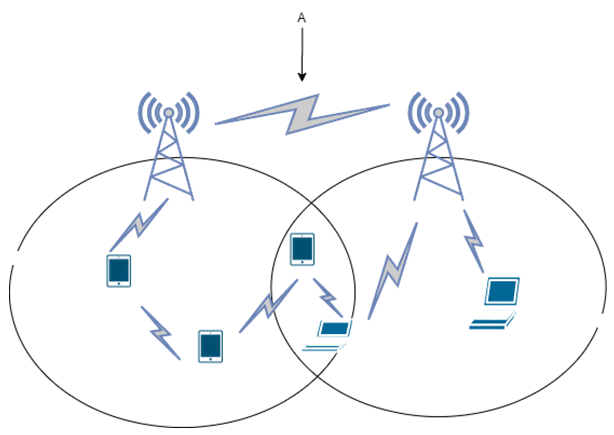
a) Centralised intra-network spectrum sharing
b) Centralised inter-network spectrum sharing
c) Distributed inter-network spectrum sharing
d) Distributed intra-network spectrum sharing
View Answer
Explanation: xG networks are generally overlapped to maximize the opportunistic usage of a licensed spectrum band. An example of a centralized inter-network approach is the common spectrum coordination channel protocol designed to support the combined existence of IEEE 802.11b and IEEE 802.16a.
Sanfoundry Global Education & Learning Series – Cognitive Radio.
To practice all areas of Cognitive Radio, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
