This set of Cognitive Radio Multiple Choice Questions & Answers focuses on “Building CRA on SDR Architecture – 2”.
1. Which among the following is a challenge in security management?
a) Authentication
b) Validation
c) Encryption and decryption
d) Balancing convenience and security
View Answer
Explanation: Security management is controlled by the system control unit. It is responsible for protecting the user data using various safety measures such as encryption. Security management must carefully balance convenience and security. This can be a timing consuming process.
2. Which among the following is not a common feature between virtual channel management and network management?
a) Identification of resources
b) Verification of availability of resources
c) Matching resources with requirements of application
d) Applicable for radio resources
View Answer
Explanation: Direct virtual channel management is responsible for identifying and verifying radio resources. It finds channels to transmit information, determines channels to listen for information, determines the channels that can be used simultaneously, etc. The network management performs the same operation on digital paths, not on radio resources.
3. What is used by the cognitive radio to justify the usage of resources?
a) Computational model
b) Component cycle
c) Function cycle
d) Cognition model
View Answer
Explanation: A computational model is used by the cognitive radio to keep track and to justify the usage of internal resources. The computational model consists of analog and digital parameters of performance. It also establishes the relationship between parameters on the basis of measurement and control.
4. Which among the following is used to represent interdependencies in cognitive radio?
a) Representation language
b) Constraint language
c) Ontology language
d) Modelling language
View Answer
Explanation: The cognitive radio learns from the data structures of various phases of the cognition cycle and inference hierarchy to determine relationships among the information that would benefit the user. Constraint languages may be used to express the interdependencies found in the information. For example, constraint language may be used to express the number of channels supported by the radio hardware during failure mode.
5. Which among the following caused the shift of complexity management from networks to cognitive radio?
a) Introduction of multiple bands in radio
b) Introduction of multiple modes in radio
c) Introduction of multiple bands and multiple modes in radio
d) Elimination of multiple bands in radio
View Answer
Explanation: The transition from software defined radio to cognitive radio is due to the availability of resources and technology that allow the incorporation of awareness, adaptability, and cognition skills in the radio. For example, cellular networks manage the wireless protocols for the user but the emergence of cognitive radio with the capability of supporting multiple bands and modes shift the responsibility of protocol management towards the radio itself.
6. What is parallel virtual machine?
a) Parallel virtual machine is a centralised computing system developed by joining a set of serial computers
b) Parallel virtual machine is a distributed computing system developed by joining a set of parallel computers
c) Parallel virtual machine is a centralised computing system developed by joining a set of parallel computers
d) Parallel virtual machine is a distributed computing system developed by joining a set of serial computers
View Answer
Explanation: A parallel virtual machine is a distributed computing system developed by joining a set of parallel computers into a single virtual machine. Complex computational problems may be solved more efficiently by utilizing collective power and memory of many computers. It may be used for resource allocation in cognitive radio.
7. Which among the following may be inferred by analysing temporal properties of simultaneous processes?
a) Time difference of transmission
b) Timeout in fault tolerant systems
c) Time of arrival in receiver
d) Time difference of arrival in receiver
View Answer
Explanation: The examination of temporal properties of simultaneous processes may determine timeout in fault tolerant systems, duration control in real time systems, etc. It may be regarded as a logic-based approach for reasoning about time. It may be employed for planning activities in cognitive radio.
8. Which among the following programming styles approach a problem as a series of constraints imposed on a possible solution?
a) Linear programming
b) Constraint programming
c) Object oriented programming
d) Aspect oriented programming
View Answer
Explanation: Constraint programming approaches a problem as a series of constraints imposed on a possible solution. Constraint based scheduling is a method that uses constraint programming to solve scheduling problems. It may be used as a planning tool in cognitive radio.
9. Which among the following is a characteristic observed in constraint programming?
a) No changes can made on definition of the system
b) Only independent variables are applied
c) Strict norms to compute a value
d) Definition of relationship between variables and constraints
View Answer
Explanation: Constraint programming is applied to a group of problems thatpermit the conversion of a problem into variables. It should be possible to define the problem as a mathematical equation. A final model is constructed based on the relationship between the variables and the constraints. The model is used to compute the value of variables.
10. What is the T250 model of Mitsubishi?
a) Single-mode handset
b) Dual-mode handset
c) Three-mode handset
d) Four-mode handset
View Answer
Explanation: The T250 model of Mitsubishi is a three-mode handset. It operates in Time Division Multiple Access (TDMA) mode on 850 or 1900 MHz, Advanced Mobile Phone System (AMPS) mode on 850 MHz, and in Cellular Digital Packet Data (CDPD) mode on 1900 MHz. It is a primitive example of multiband, multimode wireless device.
11. Parallel virtual machine is implemented using homogeneous computers.
a) True
b) False
View Answer
Explanation: Parallel virtual machine is implemented using a set of heterogeneous computers that work as a combined and flexible computational resource. Message-passing, task and resource management, and fault notification is accomplished by using a run time environment and library. Parallel virtual machine supports unicasting, multicasting, and broadcasting.
12. Which among the following correspond to the point plotted in the graph?
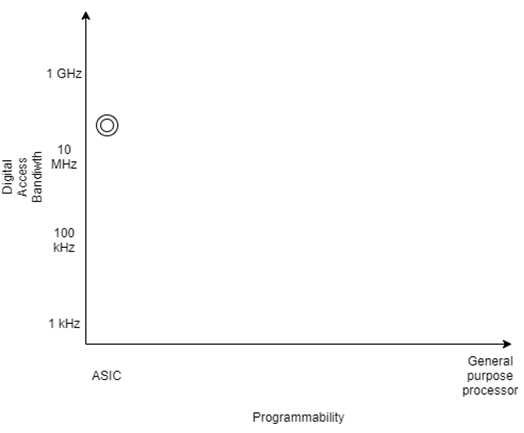
a) COTS Handset
b) Digital cell site
c) Software defined radio
d) Cognitive radio
View Answer
Explanation: The graph depicts the design space of software defined radio. The plotted point corresponds to the digital cell sites. These devices are typically constructed using Application Specific Integrated Circuits (ASICs). The devices depend greatly on digital filter ASICs for frequency translation and filtering. They access the spectrum at IF frequency.
Sanfoundry Global Education & Learning Series – Cognitive Radio.
To practice all areas of Cognitive Radio, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
