This set of Cognitive Radio Multiple Choice Questions & Answers (MCQs) focuses on “Next Generation Wireless Network – Network Cognitive Techniques”.
1. Which among the following is not a challenge identified by Situation-Aware Protocols in Edge Network Technologies developed by DARPA?
a) Knowledge representation
b) Learning
c) Composition
d) Observation
View Answer
Explanation: Situation-Aware Protocols in Edge Network Technologies (SAPIENT) was developed to determine the effectiveness of cognitive approaches to adaptive composition and the adaption of protocol structures. Knowledge representation, learning, selection, and composition are the challenges identified by SAPIENT.
2. Which among the following is not a characteristic of transactional applications?
a) Large delay
b) Timing variability
c) Small transmitted packets
d) Variably sized received packets
View Answer
Explanation: Transactional applications exhibit small packet sizes, variable sizes in received packets, and variability in timing. On the other hand, a constant packet size with inter arrival delay is typically observed in media applications.
3. Which among the following processes are combined to select protocol elements?
a) Network information and media access control information
b) Network information and application information
c) Protocol element knowledge and application information
d) Protocol element knowledge and network information
View Answer
Explanation: Protocol element knowledge is responsible for adapting to network conditions. Protocol element knowledge and application knowledge are combined to select and define protocol elements.
4. Which among the following is a network parameter that should be considered while framing a new policy?
a) Latency
b) Topology
c) Flow rate
d) Bit error rate
View Answer
Explanation: Network parameters namely packet ordering, packet checksums, packet loss, congestion, link capacity, link failure, latency, and strength of a signal on the link are essential to validate a new protocol. High end sensors can be employed to calculate hysteresis and damping algorithms to mitigate noise that provokes unwanted response.
5. Which among the following is an objective of sensing the network conditions?
a) Automatic sensing of repeaters in the route
b) Automatic detection of quality of service requirements
c) Creation of a database of application requirement
d) Measurement of parameters that maintain present working state
View Answer
Explanation: Network conditions are sensed to detect the values of parameters that are essential to maintain the present working state and also for pursuing new states. A system generally initiates with TCP/IP configuration, and modifications are applied to improve the performance. When a protocol composition is incompatible, network sensing is responsible for identifying the source of the defect as well as for selecting an appropriate protocol.
6. Which among the following is achieved by introducing virtual infrastructure beneath the transport layer?
a) Inheritance
b) Interoperability
c) Encapsulation
d) Polymorphism
View Answer
Explanation: The interoperability IP infrastructure is built based on modular programming and data abstraction. The operational challenges of a layer are confined within that layer. The data is transferred by using packets or is included as additional information in the procedural call between layers.
7. Which among the following is an objective of interoperable virtual IP infrastructure?
a) Flow control
b) Error control
c) Congestion control
d) End to end connectivity
View Answer
Explanation: The interoperable virtual IP infrastructure can combine a number of incompatible subnetworks into a virtual network. This enables the assumption that the properties of the network correspond to the end to end protocols. The internetwork is constructed over several subnetworks, and routes to provide end to end connectivity.
8. Which among the following may result in the failure of link-layer checksum?
a) Negative acknowledgment
b) Error burst
c) Route failure
d) Packet loss
View Answer
Explanation: The failure of link layer checksum determined by the device driver for a line card used to connect the host to the network indicates error bursts on a link. Likewise, a high delay in communication among a group of hosts indicates congestion.
9. Which among the following is not a parameter of influence while constructing adaption schemes for a network?
a) Compatibility of composition with objective
b) Knowledge of inherent assumptions
c) Knowledge of database evaluation
d) Knowledge of external conditions
View Answer
Explanation: The structural adaption scheme requires knowledge of external conditions that influence the protocol elements. It also requires knowledge of inherent assumptions relevant to certain protocol elements that affect its sustainability. It requires the mapping of composition with the objective to achieve the desired quality of service.
10. What are terms that should replace the label ‘A’ and ‘B’?
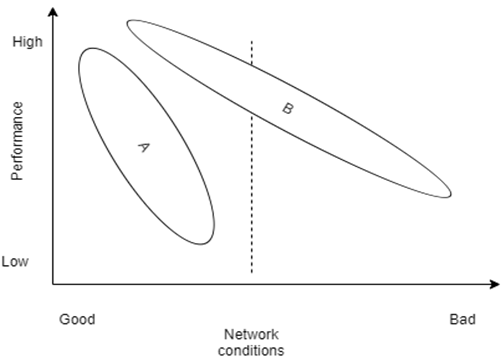
a) Predefined protocols, Rule based protocols
b) Static algorithms, Situation aware protocols
c) Situation aware protocols, Static algorithms
d) Rule based protocols, Predefined protocols
View Answer
Explanation: Under good network conditions, good throughput with low latency can be achieved with minimal protocol support. However with deteriorating channel conditions, advanced protocol mechanisms capable of adapting to the changing channel conditions required. These protocols have compensatory mechanisms extending towards applications that are not satisfied by traditional architectures.
Sanfoundry Global Education & Learning Series – Cognitive Radio.
To practice all areas of Cognitive Radio, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
