This set of Data Structures & Algorithms Multiple Choice Questions & Answers (MCQs) focuses on “Flooding Algorithm”.
1. Which among the following is a property of the flooding algorithm?
a) Robustness
b) Complex
c) Efficient
d) Flexible
View Answer
Explanation: In the flooding algorithm, all the upcoming packets on a router are sent to all the connected nodes except the one on which it has arrived. Even in case of any failure, it can deliver all the packets via the shortest route. Hence, it is robust.
2. In which layer of the computer networks is the flooding algorithm implemented?
a) Transport layer
b) Network layer
c) Application layer
d) Presentation layer
View Answer
Explanation: The network layer is responsible to transfer packets from source to destination. It must determine the best route so that the packets can be delivered through the shortest path. Hence, it uses a flooding algorithm to transmit packets quickly to every node in a large network.
3. Consider the figure given below. If a message is flooded from node A, it will reach to which of the following nodes?
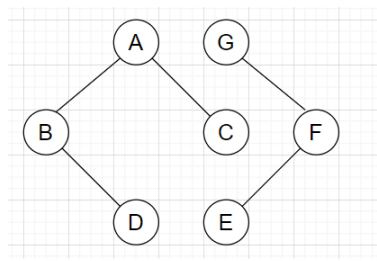
a) A, B, C, D, E, F
b) A, B, C, D, E,
c) A, B, C, D, E, F, G
d) A, B, C, D
View Answer
Explanation: A message flooding from node A, will be transmitted to node B and node C. After that, it will be transmitted to node D via node B. Node E, F, G is not connected to any of the nodes A, B, C or D. Hence, the message will reach to node A, B, C and D only.
4. Given below is the pseudocode of the flooding algorithm. Node and message are denoted by n and m respectively. Which of the following best suits the blank?
if m.id was seen before, discard else, add m.id to list of seen messages and ______
a) discard the message
b) forward the message in the direction from where it came.
c) forward the message to all neighbors of n
d) forward the message to the left neighbor of n
View Answer
Explanation: If a node receives a message that it has previously seen, it simply discards the message. However, if that is not the case, the node adds the message to the list of received messages and forwards it to all the neighboring nodes.
5. Flooding algorithm shouldn’t be used if only a single destination needs the packet.
a) True
b) False
View Answer
Explanation: In the flooding algorithm, the packets are sent to all the outgoing lines which creates a vast number of duplicate packets. Due to this, the network traffic is high with unwanted and duplicate data packets. Hence, the flooding algorithm shouldn’t be used if only a single destination needs the packet.
6. Consider the figure given below, a message is sent from A to D with a maximum hop count of 3. What will be the total number of packets sent, if the flooding algorithm is applied on node A?
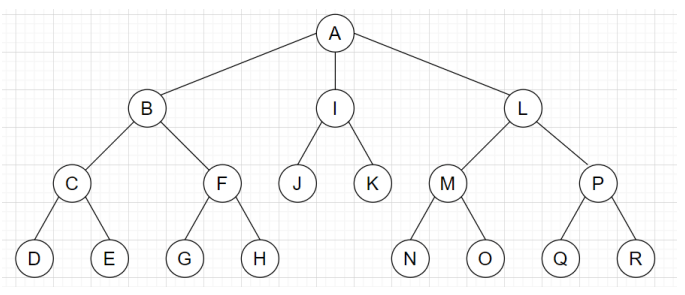
a) 17
b) 19
c) 21
d) 23
View Answer
Explanation: If the flooding algorithm is applied on node A, the message will be transmitted to node B, I and J. Similarly, node B will transmit the packet to node C and F, node I will transmit to node J and K, and node L will transmit it to node M and P. We can observe that, each edge contains at most one copy of the message. Hence, the total number of packets flooded will be equal to the total number of edges which is 17.
7. Flooding algorithm requires all the network information before implementation.
a) True
b) False
View Answer
Explanation: The flooding algorithm follows the brute force approach and sends every incoming packet on every outgoing line it is connected to. Hence, flooding algorithms do not require network information like the cost of all the paths, load conditions or the topology before implementation.
8. What will be the maximum number of rounds required to reach all nodes in the flooding algorithm?
a) Radius to the graph
b) Diameter of graph
c) 1
d) Distance between two nodes
View Answer
Explanation: The diameter of the graph is the maximum distance in a graph between any two arbitrary nodes in it. Hence, it will take at most diameter of the graph rounds for the message to reach all nodes of the graph in the flooding algorithm.
9. Which among the following is the message complexity for the flooding algorithm?
a) O(|E|)
b) O(|E2|)
c) O(n2)
d) O(1)
View Answer
Explanation: In the flooding algorithm, the message is sent to all the connected edges. It floods the message to all the neighbors. Every node sends the message to its neighbor once, so each edge carries a maximum of one copy of the message. Hence, the message complexity is the lower bound of the total number of edges, which is O(|E|).
10. Which type of flooding doesn’t send every incoming packet on every outgoing line?
a) Sequence number-controlled flooding
b) Selective flooding
c) Reverse path forwarding
d) Normal flooding
View Answer
Explanation: Selective flooding transmits the packet only in the direction of the destination, instead of sending all the incoming packets to all the outgoing lines. It is a variant of flooding. Due to this, the number of duplicate packets generated is less in number compared to the normal flooding.
Sanfoundry Global Education & Learning Series – Data Structures & Algorithms.
To practice all areas of Data Structures & Algorithms, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
- Check Programming Books
- Practice Data Structure MCQ
- Apply for Computer Science Internship
- Practice Programming MCQs
- Practice Computer Science MCQs
