This set of Cryptography Multiple Choice Questions & Answers focuses on “RC4 and RC5”.
1. RC5 encryption uses Right shift and decryption uses Left shift.
a) True
b) False
View Answer
Explanation: RC5 encryption rounds use left shift operations and the decryption uses right shift operations.
2. The below round is the last step in encryption /decryption in RC5.
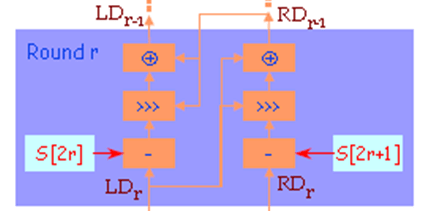
a) True
b) False
View Answer
Explanation: The last round is the last step in encryption but the first step in decryption process.
3. The code bellow is the RC5 encryption pseudo code in C language.
What is the error?
LE0 = A + S[0];
RE0 = B + S [1];
for i = 1 to r do
LEi = ((LEi-1 ⊕ REi-1) >>> REi-1) + S [2xi];
REi = ((REi-1 ⊕ LEi) <<< LEi) + S [2xi+1];
a) The left shift operation (should be right shift)
b) The right shift operation (should be left shift)
c) LEi-1 and REi-1 should be LEi and REi
d) The for loop runs from 1 to r-1 ( not 1 to r)
View Answer
Explanation:
Correct code –
LE0 = A + S[0];
RE0 = B + S [1];
for i = 1 to r do
LEi = ((LEi-1 ⊕ REi-1) <<<REi-1) + S [2xi];
REi = ((REi-1 ⊕ LEi) <<< LEi) + S [2xi+1];
4. “RC5 uses the Feistel Structure.”
a) True
b) False
View Answer
Explanation: RC5 does not use the classic Feistel structure.
5. Find the error in the Decryption pseudo code for RC5 –
for i = 1 to r do
RDi-1 = ((RDi – S [2xi+1] >>> LDi ) ⊕ LDi);
LDi-1 = ((LDi – S [2xi] >>> RDi-1) ⊕ RDi-1);
B= RD0 + S [1];
A = LD0 – S [0];
a) B= RD0 + S [1];
b) for i = 1 to r do
c) LDi-1 = ((LDi – S [2xi] >>> RDi-1) ⊕ RDi-1);
d) A = LD0 – S [0];
View Answer
Explanation: B= RD0 + S [1]; is incorrect as there should be a ‘-’ instead.
6. Which one of the following is not a RC5 mode of operation?
a) RC5 block cipher
b) RC5-Cipher Block Chaining
c) RC5-Cipher Padding
d) RC5-CipherText Stealing
View Answer
Explanation: RFC 2040 [BALD96] defines four different modes of operation:
1. RC5 block cipher
2. RC5-CBC
3. RC5-CBC-Pad
4. RC5-CTS.
7. Which RC5 mode will have the ciphertext longer than the plaintext by at most the size of a single RC5 block?
a) RC5 block cipher
b) RC5-Cipher Block Chaining
c) RC5-Cipher Block Chaining Pad
d) RC5-CipherText Stealing
View Answer
Explanation: The Cipher Block Chaining Pad mode produces a ciphertext output as such.
8. Which RC5 mode of operation is this?
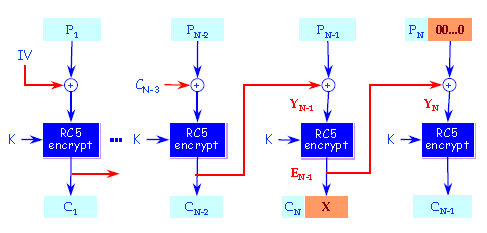
a) RC5 block cipher
b) RC5-Cipher Block Chaining
c) RC5-Cipher Block Chaining Pad
d) RC5-CipherText Stealing
View Answer
Explanation: This mode of operation is the RC5 CTS mode.
9. Which of these is not a characteristic of block ciphers?
a) Variable key length / block size / number of rounds
b) Mixed operators, data/key dependent rotation
c) Key independent S-boxes
d) More complex key scheduling
View Answer
Explanation:
Features seen in modern block ciphers are:
– Variable key length / block size / number of rounds
– Mixed operators, data/key dependent rotation
– Key dependent S-boxes
– More complex key scheduling
– Operation of full data in each round
– Varying non-linear functions.
10. Which one of the following RC4 algorithm not used in?
a) SSL
b) TLS
c) FTP
d) WEP
View Answer
Explanation: RC4 is used in Secure Socket Layer, Transport Layer Security and Wired Equivalency Privacy. Not used in File Transfer Protocol.
11. Till when was the RC4 algorithm kept a secret?
a) 1990
b) 1992
c) 1996
d) 1994
View Answer
Explanation: In September 1994, the RC4 algorithm was anonymously posted on the Internet on the Cypherpunks anonymous remailers list.
12. RC4 algorithm uses the concept of Block Cipher System.
a) True
b) False
View Answer
Explanation: RC4 algorithm uses the concept of Stream Cipher and uses a “stream key”.
Sanfoundry Global Education & Learning Series – Cryptography and Network Security.
To practice all areas of Cryptography, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
- Check Cryptography and Network Security Books
- Practice Computer Science MCQs
- Check Computer Science Books
- Practice Cyber Security MCQ
- Apply for Computer Science Internship
