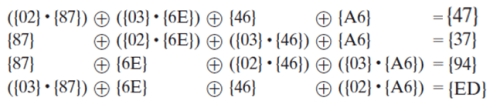This set of Cryptography Inteview Questions and Answers for freshers focuses on “The AES Algorithm”.
1. How many step function do Round 1 and 2 each have in S-AES?
a) 4 and 3
b) Both 4
c) 1 and 4
d) 3 and 4
View Answer
Explanation: Round 1 has four step functions whereas Round 2 has three step functions.
2. For a key 25D5 and PT input A479 what is the output we obtain after the “add round key” function?
a) F34D
b) 81AC
c) 79DF
d) 327D
View Answer
Explanation: Simply apply XOR to the state matrix PT with the key matrix to obatain the output which in this case is 81AC.
3. The output of the previous question, on passing through “nibble substitution” gets us the output
a) 3267
b) 1344
c) 64C0
d) CA37
View Answer
Explanation: 81AC after passing through the “nibble substitution” round produces an output 64C0. A corresponding substitution is referred to in this step.
4. The output of the previous question on passing through the “shift row” step function gives us the output
a) C046
b) 0C64
c) 64C0
d) 640C
View Answer
Explanation: 64C0 after passing through the “shift row” round produces an output 640C. A one nibble shift is performed in the second row in this step.
5. The output of the previous question on passing through the “mix columns” step function gives us the output
a) 3252
b) 3743
c) 3425
d) 3473
View Answer
Explanation: 64C0 after passing through the “mix columns” round produces an output 3473. This is obtained by multiplying this matrix with the matrix 1441.
6. On performing the mix column transformation on the matrix
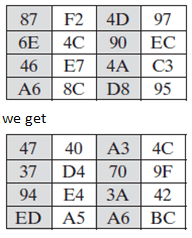
(Verify for the first column only)
a) True
b) False
View Answer
7. The inverse transformation matrix times the forward transformation matrix equals the identity matrix.
a) True
b) False
View Answer
Explanation: The statement is true. The inverse transformation matrix times the forward transformation matrix does equal the identity matrix.
8. Which of the following are true?
i) In the AES key expansion algorithm, the function g() operates on w i+3
ii) Perform a one-byte right circular rotation on the argument 4-byte word
iii) The round constant follows the formula RC[j] = RC[j − 1]
a) i) ii)
b) ii) only
c) i) only
d) All
View Answer
Explanation: Only the first option is true. There is a left circular rotation in AES key expansion. RC[j] = 2 × RC [j − 1] is the formula for the round constant.
9. How many round keys are generated in the AES algorithm?
a) 11
b) 10
c) 8
d) 12
View Answer
Explanation: 11 round keys are generated. One for each of the 10 rounds and one of the initial permutations (Round 0).
10. Which function can be used in AES multiplication
a) m(x)=x7+x4+x3
b) m(x)=x8+x4+x3+x+1
c) m(x)=x8+x3+x2+x+1
d) m(x)=x8+x5+x3+x
View Answer
Explanation: m(x)=x8+x4+x3+x+1 stands for 100011011 which is an irreducible polynomial. Others are not irreducible polynomials.
Sanfoundry Global Education & Learning Series – Cryptography and Network Security.
To practice all areas of Cryptography for interviews, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
- Check Computer Science Books
- Practice Cyber Security MCQ
- Apply for Computer Science Internship
- Check Cryptography and Network Security Books
- Practice Computer Science MCQs