This set of Cryptography Multiple Choice Questions & Answers (MCQs) focuses on “DES Modes of Operation”.
1. How many modes of operation are there in in DES and AES?
a) 4
b) 3
c) 2
d) 5
View Answer
Explanation: DES has 5 modes of operation.
2. Which one of the following modes of operation in DES is used for operating short data?
a) Cipher Feedback Mode (CFB)
b) Cipher Block chaining (CBC)
c) Electronic code book (ECB)
d) Output Feedback Modes (OFB)
View Answer
Explanation: The Electronic code book mode is used for operating on short data as the same key is used for each block. Thus repetitions in Plain Text lead to repetitions in Cipher Text.
3. Which of the following is false for ECB mode of operation
i) The Plain text is broken into blocks of size 128 bytes
ii) Blocks can be swapped, repeated, replaced without recipient noticing
iii) Good for short data
iv) Encryption of each block is done separately using a randomly generated key for each block
a) i) only
b) ii) and iii)
c) i) and iv)
d) i) ii) and iv)
View Answer
Explanation: Block size is 64 bits. The same Key is used for each block.
4. Which of the following statements are true
i) In the CBC mode, the plaintext block is XORed with previous ciphertext block before encryption
ii) The CTR mode does not require an Initialization Vector
iii) The last block in the CBC mode uses an Initialization Vector
iv) In CBC mode repetitions in plaintext do not show up in ciphertext
a) iii)
b) ii) and iv)
c) All the Statements are true
d) i) ii) and iv)
View Answer
Explanation: The first block in CBC mode uses an IV.
5. There is a dependency on the previous ‘s’ bits in every stage in CFB mode. Here ‘s’ can range from ___
a) 8-16 bits
b) 8-32 bits
c) 4-16 bits
d) 8-48 bits
View Answer
Explanation: The range of the output of each stage of the cipher system is 8-32 bits for a 64 bit system.
6. What is the fault in the above figure?
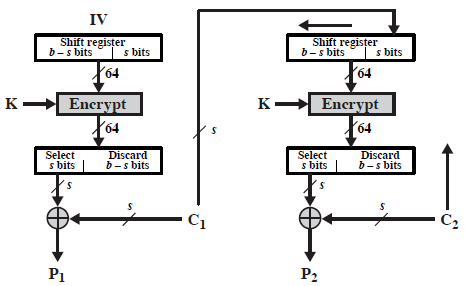
a) The output of the XOR is sent to the next stage
b) The “Encrypt” Box should be replaced by “Decrypt Box
c) b-s bits are selected for the XOR operation
d) No fault
View Answer
Explanation: The algorithm is the Decryption algorithm for Cipher Feedback Mode (CBF)
7. Which of the following can be classified under advantages and disadvantages of OFB mode?
i) Transmission errors
ii) A bit error in a ciphertext segment
iii) Cannot recover from lost ciphertext segments
iv) Ciphertext or segment loss
a) Advantages: None; Disadvantages: All
b) Advantages: All; Disadvantages: None
c) Advantages: i); Disadvantages: ii) iii) iv)
d) Advantages: i); ii) Disadvantages: iii) iv)
View Answer
Explanation: Advantages:
More resistant to transmission errors.
A bit error in a ciphertext segment affects only the decryption of that segment.
Disadvantages:
Cannot recover from lost ciphertext segments.
If a ciphertext segment is lost, all following segments will be decrypted incorrectly (if the receiver is not aware of the segment loss).
8. In OFB Transmission errors do not propagate: only the current ciphertext is affected, since keys are generated “locally”.
a) True
b) False
View Answer
Explanation: Yes, transmission errors do not propagate in OFB mode because of the locally generated key.
9. Which of the following modes does not implement chaining or “dependency on previous stage computations”?
a) CTR, ECB
b) CTR, CFB
c) CFB, OFB
d) ECB, OFB
View Answer
Explanation: Only CTR and ECB do not implement chaining.
10. The counter value in CTR modes repeats are a regular interval.
a) True
b) False
View Answer
Explanation: The Counter value in CTR mode should never be repeated, else it leads to vulnerability of the mode. We must ensure never reuse key/counter values; otherwise it could break (OFB).
Sanfoundry Global Education & Learning Series – Cryptography and Network Security.
To practice all areas of Cryptography and Network Security, here is complete set of 1000+ Multiple Choice Questions and Answers
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
- Practice Computer Science MCQs
- Practice Cyber Security MCQ
- Check Computer Science Books
- Check Cryptography and Network Security Books
- Apply for Computer Science Internship
