This set of Network Security Interview Questions and Answers focuses on “Topologies”.
1. Which network topology does this represent?
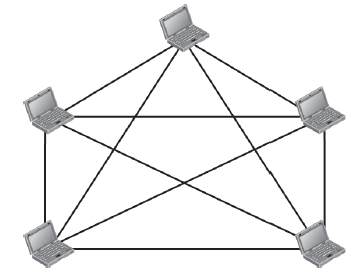
a) Mesh
b) Star
c) Bus
d) Ring
View Answer
Explanation: The figure represents the mesh topology.
2. ‘Jitter’ refers to-
a) errorless delivery
b) variation in the packet arrival time
c) timely delivery of message
d) none of the mentioned
View Answer
Explanation: ‘Jitter’ refers to variation in the packet arrival time.
3. 2 Half duplex systems can make a Full-Duplex.
a) True
b) False
View Answer
Explanation: The statement is true.
4. Which topology requires the most amount of wiring?
a) Mesh
b) Star
c) Bus
d) Ring
View Answer
Explanation: This is the disadvantage of mesh topology.
5. How many links are there for N nodes in the mesh topology?
a) 1
b) N(N+1)/2
c) N
d) N(N-1)/2
View Answer
Explanation: There are N(N-1)/2 links for N nodes.
6. Which topology has a central hub?
a) Mesh
b) Star
c) Bus
d) Ring
View Answer
Explanation: The star topology has a single hub.
7. Which topology has the toughest fault identification?
a) Mesh
b) Star
c) Bus
d) Ring
View Answer
Explanation: In the bus topology, fault identification is tougher.
8. Ethernet LANs use which topology?
a) Mesh
b) Star
c) Bus
d) Ring
View Answer
Explanation: Ethernet LANs use bus topology,
9. Which topology uses the token passing algorithm?
a) Mesh
b) Star
c) Bus
d) Ring
View Answer
Explanation: The ring topology uses the token passing algorithm. The token holder gets its turn at communication.
10. How many lines are required for the bus topology?
a) N(N-1)/2
b) N
c) N+1
d) none of the mentioned
View Answer
Explanation: N drop lines and 1 bus line.
11. A list of protocols used is known as –
a) protocol access
b) protocol stack
c) permutation stack
d) none of the mentioned
View Answer
Explanation: A list of the protocols used by a certain system, one protocol per layer, is called a protocol stack.
12. In order to prevent a fast sender from swamping a slow receiver with data, feedback is often used. This process is known as-
a) flow control
b) multiplexing
c) congestion
d) none of the mentioned
View Answer
Explanation: The process defined above is known as Flow Control.
Sanfoundry Global Education & Learning Series – Cryptography and Network Security.
To practice all areas of Network Security for Interviews, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
- Apply for Computer Science Internship
- Practice Computer Science MCQs
- Practice Cyber Security MCQ
- Check Computer Science Books
- Check Cryptography and Network Security Books
