This set of Cryptography Problems focuses on “Public Keys and X.509 Certificates”.
1. How many handshake rounds are required in the Public-Key Distribution Scenario?
a) 7
b) 5
c) 3
d) 4
View Answer
Explanation: A total of seven messages are required in the Public-Key distribution scenario.
2. A total of seven messages are required in the Public-Key distribution scenario. However, the initial five messages need to be used only infrequently because both A and B can save the other’s public key for future – a technique known as ____
a) time stamping
b) polling
c) caching
d) squeezing
View Answer
Explanation: This technique is known as caching.
3. X.509 certificate recommends which cryptographic algorithm?
a) RSA
b) DES
c) AES
d) Rabin
View Answer
Explanation: RSA is the recommended cryptographic algorithm for X.509 certificates.
4. The issuer unique identifier of the X.509 certificates was added in which version?
a) 1
b) 2
c) 3
d) 4
View Answer
Explanation: The issuer unique identifier was added in the 2nd version.
5. The period of validity consists of the date on which the certificate expires.
a) True
b) False
View Answer
Explanation: The Period of validity consists of 2 dates: the first and last date on which the certificate is valid.
6. Certificate extensions fall into 3 categories. Which one of the following is not a Certificate extensions category?
a) Subject and Issuer attributes
b) Key and Policy information
c) Certification path constraints
d) All of the above are Certificate extensions categories
View Answer
Explanation: Subject and Issuer attributes, Key and Policy information and Certification path constraints are the three categories of Certificate extensions.
7. What does the above figure represent?
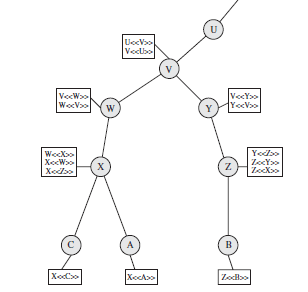
a) Hierarchical in X.509
b) IPsec connectivity
c) TCP nodes and links
d) None of the mentioned
View Answer
Explanation: The figure is a representation of Hierarchy in X.509.
8. How many functions are involved in the PKIX architectural model?
a) 3
b) 5
c) 6
d) 7
View Answer
Explanation: The 7 functions are: Registration, Initialization, Certification, Key pair recovery, Key pair update, Revocation request and Cross certification.
9. CMP stands for
a) cipher message protocol
b) cipher management protocol
c) certificate message protocol
d) none of the mentioned
View Answer
Explanation: CMP stands for certificate management protocol.
10. CMS stands for
a) cipher message syntax
b) certificate message session
c) cryptographic message syntax
d) none of the mentioned
View Answer
Explanation: CMS stands for cryptographic message syntax.
Sanfoundry Global Education & Learning Series – Cryptography and Network Security.
To practice problems on all areas of Cryptography, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
- Practice Cyber Security MCQ
- Apply for Computer Science Internship
- Check Cryptography and Network Security Books
- Check Computer Science Books
- Practice Computer Science MCQs
