This set of Cryptography Quiz focuses on “Blowfish Algorithm”.
1. In blowfish, the keys are stored in the form of an array ranging from K1, K2 to Ki. What is the value of i?
a) 12
b) 16
c) 8
d) 14
View Answer
Explanation: The keys are stored in an K-array
K_1,K_2,,,,,,,K_J 1≤J≤14.
2. To generate the sub-key P1 to P18 we use the hexadecimal equivalent digits of ____________
a) 0.7864
b) 0.1415
c) 0.1542
d) 0.7535
View Answer
Explanation: To generate the sub-key P1 to P18 we use the hexadecimal equivalent digits of Pi-3 (only the decimal part).
3. P17 gets XORed with
a) K3
b) K12
c) K17
d) K6
View Answer
Explanation: XOR P1 with the key K1, XOR P2 with K2, and so on for all bits of the key (possibly up to P14). Repeatedly cycle through the key bits until the entire P-array has been XORed with key bits.
4. P15 gets XORed with
a) K3
b) K14
c) K1
d) K6
View Answer
Explanation: XOR P1 with the key K1, XOR P2 with K2, and so on for all bits of the key (possibly up to P14). Repeatedly cycle through the key bits until the entire P-array has been XORed with key bits.
5. What is the number of iterations required in total to generate all the sub-keys in blowfish?
a) 512
b) 521
c) 256
d) 128
View Answer
Explanation: In total, 521 iterations are required to generate all required subkeys(i.e. 9 rounds for P1-P18 and 512 rounds for S1-S4).
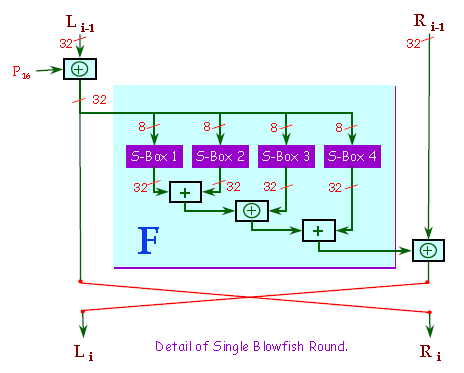
6. A single blowfish s-box converts 8-bits to _________ bits.
a) 32
b) 44
c) 56
d) 64
View Answer
7. The 32bit output of s-box 1 is XORed with s-box 2.
a) True
b) False
View Answer
Explanation: The 32bit output of s-box 1 is added with s-box 2.
8. Which of the following statements are true with respect to the blowfish algorithm –
i) Provided key is large enough, brute-force key search is not practical, especially given the high key schedule cost
ii) Key dependent S-boxes and sub keys make analysis very difficult
iii) Changing both halves in each round increases security
iv) Blowfish has improved avalanche effects
a) i) ii) and iv)
b) ii) and iii)
c) i)
d) All are true
View Answer
Explanation: All of the above statements are true with respect to the blowfish algorithm.
Sanfoundry Global Education & Learning Series – Cryptography and Network Security.
To practice all areas of Cryptography for quizzes, here is complete set of 1000+ Multiple Choice Questions and Answers
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
- Apply for Computer Science Internship
- Check Computer Science Books
- Check Cryptography and Network Security Books
- Practice Cyber Security MCQ
- Practice Computer Science MCQs