This set of Cyber Security Multiple Choice Questions & Answers (MCQs) focuses on “Elements of Security”.
1. In general how many key elements constitute the entire security structure?
a) 1
b) 2
c) 3
d) 4
View Answer
Explanation: The 4 key elements that constitute the security are: confidentiality, integrity, authenticity & availability. Authenticity is not considered as one of the key elements in some other security models, but the popular CIA Triad eliminates this as authenticity at times comes under confidentiality & availability.
2. According to the CIA Triad, which of the below-mentioned element is not considered in the triad?
a) Confidentiality
b) Integrity
c) Authenticity
d) Availability
View Answer
Explanation: According to the CIA triad the three components that a security need is the Confidentiality, Integrity, Availability (as in short read as CIA).
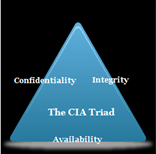
3. This is the model designed for guiding the policies of Information security within a company, firm or organization. What is “this” referred to here?
a) Confidentiality
b) Non-repudiation
c) CIA Triad
d) Authenticity
View Answer
Explanation: Various security models were being developed till date. This is by far the most popular and widely used model which focuses on the information’s confidentiality, integrity as well as availability and how these key elements can be preserved for a better security in any organization.
4. CIA triad is also known as ________
a) NIC (Non-repudiation, Integrity, Confidentiality)
b) AIC (Availability, Integrity, Confidentiality)
c) AIN (Availability, Integrity, Non-repudiation)
d) AIC (Authenticity, Integrity, Confidentiality)
View Answer
Explanation: This approach of naming it CIA Triad as AIC (Availability, Integrity, Confidentiality) Triad because people get confused about this acronym with the abbreviation and the secret agency name Central Intelligence Agency.
5. When you use the word _____ it means you are protecting your data from getting disclosed.
a) Confidentiality
b) Integrity
c) Authentication
d) Availability
View Answer
Explanation: Confidentiality is what every individual prefer in terms of physical privacy as well as digital privacy. This term means our information needs to be protected from getting disclose to unauthorised parties, for which we use different security mechanisms like password protection, biometric security, OTPs (One Time Passwords) etc.
6. ______ means the protection of data from modification by unknown users.
a) Confidentiality
b) Integrity
c) Authentication
d) Non-repudiation
View Answer
Explanation: A information only seems valuable if it is correct and do not get modified during its journey in the course of arrival. The element integrity makes sure that the data sent or generated from other end is correct and is not modified by any unauthorised party in between.
7. When integrity is lacking in a security system, _________ occurs.
a) Database hacking
b) Data deletion
c) Data tampering
d) Data leakage
View Answer
Explanation: The term data tampering is used when integrity is compromised in any security model and checking its integrity later becomes costlier. Example: let suppose you sent $50 to an authorised person and in between a Man in the Middle (MiTM) attack takes place and the value has tampered to $500. This is how integrity is compromised.
8. _______ of information means, only authorised users are capable of accessing the information.
a) Confidentiality
b) Integrity
c) Non-repudiation
d) Availability
View Answer
Explanation: Information seems useful only when right people (authorised users) access it after going through proper authenticity check. The key element availability ensures that only authorised users are able to access the information.
9. Why these 4 elements (confidentiality, integrity, authenticity & availability) are considered fundamental?
a) They help understanding hacking better
b) They are key elements to a security breach
c) They help understands security and its components better
d) They help to understand the cyber-crime better
View Answer
Explanation: The four elements of security viz. confidentiality, integrity, authenticity & availability helps in better understanding the pillars of security and its different components.
10. This helps in identifying the origin of information and authentic user. This referred to here as __________
a) Confidentiality
b) Integrity
c) Authenticity
d) Availability
View Answer
Explanation: The key element, authenticity helps in assuring the fact that the information is from the original source.
11. Data ___________ is used to ensure confidentiality.
a) Encryption
b) Locking
c) Deleting
d) Backup
View Answer
Explanation: Data encryption is the method of converting plain text to cipher-text and only authorised users can decrypt the message back to plain text. This preserves the confidentiality of data.
12. Which of these is not a proper method of maintaining confidentiality?
a) Biometric verification
b) ID and password based verification
c) 2-factor authentication
d) switching off the phone
View Answer
Explanation: Switching off the phone in the fear of preserving the confidentiality of data is not a proper solution for data confidentiality. Fingerprint detection, face recognition, password-based authentication, two-step verifications are some of these.
13. Data integrity gets compromised when _____ and _____ are taken control off.
a) Access control, file deletion
b) Network, file permission
c) Access control, file permission
d) Network, system
View Answer
Explanation: The two key ingredients that need to be kept safe are: access control & file permission in order to preserve data integrity.
14. ______ is the latest technology that faces an extra challenge because of CIA paradigm.
a) Big data
b) Database systems
c) Cloud storages
d) Smart dust
View Answer
Explanation: Big data has additional challenges that it has to face because of the tremendous volume of data that needs protection as well as other key elements of the CIA triad, which makes the entire process costly and time-consuming.
15. One common way to maintain data availability is __________
a) Data clustering
b) Data backup
c) Data recovery
d) Data Altering
View Answer
Explanation: For preventing data from data-loss, or damage data backup can be done and stored in a different geographical location so that it can sustain its data from natural disasters & unpredictable events.
Sanfoundry Global Education & Learning Series – Cyber Security.
To practice all areas of Cyber Security, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
- Check Cyber Security Books
- Practice Programming MCQs
- Practice Computer Science MCQs
- Apply for Computer Science Internship
- Check Programming Books
