In this tutorial, you will learn the basics of computer networking, including its definition, advantages, applications, and working. You will understand how computer networks work and why it is useful nowadays.
Contents:
- What is a Computer Network?
- Components of Computer Network
- How does Computer Network work?
- How Topologies are used in Computer Network?
- Types of Computer Networks
- Protocols and Standards
- Characteristics of Computer Network
- Uses of Computer Network
What is a Computer Network?
Computer Network is an interconnection of different computers to share resources through a communication medium between them.
- Merely connecting computers is not called as computer network. For that, the connected end devices must exchange information. Therefore, two computers are said to be interconnected if and only if they both can exchange information with each other through media.
- Email, Video conferences, instant messages, and online games are an example of computer networks.
The architecture of Computer Network is shown in the below diagram:
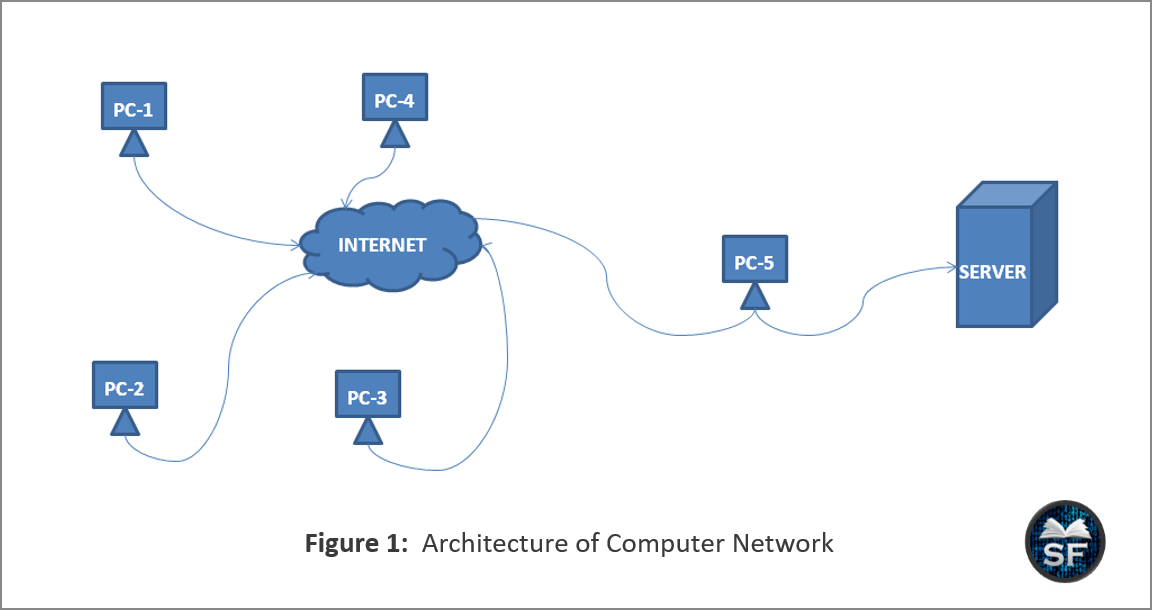
The above diagram describes the architecture of a computer network. Many computers are connected in a network to share software (Google Drive), hardware (scanner, web-cams, and printers, etc.), and data (video, audio, or text) through a communication medium between them.
Components of Computer Network
Hosts, intermediary devices, and media are components of a computer network. Host connects with intermediary devices through media to establish communication with other host and exchange information.
Hosts: Generally, computers that are connected to network communication are called hosts. Hosts are also known as end devices or clients.
- Whenever a host connects to the internet, it gets a unique number to communicate, which is known as the Internet Protocol (IP) address. Here, an IP address is used to identify the host uniquely on a network.
Intermediary Devices: To connect end devices to a network, Intermediary devices are used. By connecting multiple end devices, they form an Internetwork.
- Router, Switch, and Firewall are an example of Intermediary Devices.
Media: Whatever data you send over the Internet is transmitted through the media, and the goal of media is to provide a channel on which messages can pass from sender to receiver.
- Mainly, there are two types of media. The first is Guided Media and the second is Unguided Media.
- Guided media (coaxial cable, twisted pair cable, and fiber optics) require a physical path to establish communication between the end devices, while unguided media (radio waves, microwaves, and infrared) don’t require a physical path.
Now we got an idea about media, so let’s see four main criteria of media for choosing a network.
- How much maximum distance can media carry?
- The environment around the media.
- Speed and the amount of data.
- The expense of the media.
The below diagram describes about the components of a computer network:

As shown in the above figure, hosts are connected to intermediary devices through communication media. You can see that PC-1, PC-2, PC-3, Server, and Switch are creating one network, and it is protected by a firewall that filters bad packets.
How does Computer Network work?
The working of a computer network is as follows:
Suppose two end devices want to communicate with each other on a network. For that, both the devices will connect their NIC (Network Interface Card) through media to the intermediate device’s ports present in the network.
As both end devices connect to the network, they receive a unique number called an IP (Internet Protocol) address. After receiving an IP address, the sender end device will send its message to the intermediary devices, and according to the IP addresses of the sender and receiver, the intermediary devices decide the path and transmit the message through the media to the receiver.
The below diagram describes the IP addresses of hosts on a network:

The above diagram shows that hosts on a network are uniquely identified with the help of an IP address. It also states that there are multiple devices on the network, but they must have a unique IP address, with which we can know a particular network address for a particular host.
How are Topologies used in Computer Network?
Topology is a clear visual representation of a network, which helps visualize data communication between devices.
Generally, there are two types of topologies. They are: Physical topology and Logical topology
- Physical topology: With the help of a physical topology diagram, one can get an idea about where intermediary devices are located and where cables are installed.
- Logical topology: Using a logical topology diagram, one can understand about ports and addresses of devices that are used in a network.
It is advisable and necessary for a network administrator to visualize the network using topologies before creating a physical network. With the help of topology, you can get to know your network better and improve it.
Types of Computer Networks
Mainly, there are 4 types of Computer Networks widely used in the world. They are:
- PAN (Personal Area Network)
- LAN (Local Area Network)
- MAN (Metropolitan Area Network)
- WAN (Wide Area Network)
The following diagram describes about types of computer networks:

The above diagram shows that there are mainly four types of computer networks. These 4 networks are widely used in the world. This diagram tells us that the Internet is divided into 4 parts, and by combining each, the computer network is made.
The following table describes the features of different types of networks.
| Features | PAN | LAN | MAN | WAN |
|---|---|---|---|---|
| Definition | It is used for personal networks. | It Connects devices that are in a small geographical area to share resources at high speed. | It is larger than LAN, but it is smaller than WAN. | WAN is a collection of multiple MAN networks. It covers a large geographical area like state or country. |
| Range | < 15 meters | 150m < LAN < 10km | MAN <= 100 km | No limit |
| Bandwidth | High | High | Moderate | Low |
| Cost | Very Cheap | Less Cost | Medium Costly | High Cost |
| Error Chances | Very Low | Low | Medium | High |
| Uses | Bluetooth, Wi-Fi, USB, etc. | School, College, or Office Networks. | City Network | Country or global network |
| Delay | Less | Less | Moderate | Less |
| Speed | 1 – 5 Mbps | 10 Mbps to 1 Gbps | 10 – 100 Mbps | 5 – 20 Mbps |
Protocols and Standards
Protocols help two entities communicate with each other, and standards provide essential guidelines for the exchange of information.
Protocols: When two entities communicate with each other, they agree on some rules for making communication successful, and that set of rules is known as a Protocol. It determines how, when, and what is to be communicated.
- There are so many protocols, and they all have their own characteristics. For example, HTTP and HTTPS are used in the client & server mechanism when a client wants to access some pages or services of a website from a server.
- Likewise, FTP is used for file transfer, TELNET & SSH is used for remote access, TCP & UDP is used for connection-oriented and connectionless services respectively. Similarly, different protocols are used for different purposes.
Standards: Standards provide guidelines to organizations, manufactures, vendors, agencies, and service providers. It means that if an organization has made a product following the guidelines, then that product has standards.
- Suppose if a car company makes a car, they follow some rules and guidelines. So that one can say that this car has standards.
- ISO, ITU-T, ANSI, IEEE, and EIA are standards organizations that are used for data communication.
Characteristics of Computer Network
Typically, there are 4 characteristics of a computer network. They are Fault Tolerance, Scalability, Quality of Service, and Network Security.
Fault Tolerance: Multiple paths exist between the sender and the receiver. Therefore, in case of a path failure, the sender can send his message to the receiver via another path.
Scalability: You can expand your network whenever you need. If you want to add new users or devices to the network, you can easily scale your network without affecting the original network.
Quality of Service: It mainly focuses on managing congestion on a network. QoS provides reliability to the users.
Network Security: Use for providing good network connectivity and prevents unauthorized access.
Network Security primarily focuses on three main criteria:
- Confidentiality: Information that is personal to the user.
- Data Integrity: The data is fully transmitted or not transmitted at all.
- Availability of Data: Whenever users require data, it must be available.
In the below diagram, the characteristics of a computer network are explained.

In the above figure, the sender sends a message to a receiver via Router-1. Unfortunately, that path is broken. So, the sender sends his message via a router-2 path, this is known as fault-tolerance.
Between the transmission of a message, an attacker is trying to access data on a path. Due to the security of data, he failed to get data. Also, one can expand their network by adding new devices to the network.
Uses of Computer Network
There are mainly 3 uses of computer networks, which are Business Applications, Home Applications, and Mobile user applications.
Business Applications:
- In a company, none of them individually needs a private printer. So, one good use of Computer Network is a group of common employees sharing a common printer.
- VPNs are used to join individual networks at different sites.
- The client and server model is used if a client wants to access some services of a server.
- Companies use VoIP (Voice over IP) for saving their telephone bills.
- E-commerce provides a way for an organization to interact with consumers.
Home Applications:
- Users can connect with their home computers using remote access.
- Peer-to-peer connection is used when both sender and receiver act as client and server simultaneously.
- Via IP Television systems, TV shows now reach many houses.
- Smoke detectors sense the presence of smoke and automatically warn when any smoke is detected.
- Radio Frequency Identification (RFID) is used to identify and track objects, and the objects can be anything like books, cars, etc.
Mobile Users:
- Wireless networks such as OLA or military mobile communications.
- Text Messaging apps such as FB messenger, Instagram, WhatsApp, Viber, and email.
- Smartphones combine aspects of mobile computers and mobile phones.
- GPS is used when you want to find a café, restaurant, hospital, or petrol pump near you.
- The sensor network monitors the data in different locations.
- Wearable computers like Smartwatches, Fitness trackers, Google glass, etc.
Key Points to Remember
Here is the list of key points we need to remember about “Computer Networking”.
- Computer Network is an interconnection of different computers to share resources through a communication medium between them.
- Computer Network is made up of end devices, intermediary devices, and media, and it follows Protocols and Standards.
- An IP address is used to uniquely identify a host on a network.
- It is better to make the topology of your network before you implement it physically.
- PAN, LAN, MAN, and WAN – are types of Computer networks.
- Fault tolerance, Scalability, Quality of Service, and Security are characteristics of a Computer Network.
- Computer Network has many applications such as e-commerce, email, VoIP, remote access, and instant messaging, etc.
