This set of Interview Questions and Answers focuses on “IDaaS – Identify as a Service – 1”.
1. Salesforce.com is the largest ______ provider of CRM software.
a) PaaS
b) IaaS
c) CaaS
d) SaaS
View Answer
Explanation: Salesforce.com extended its SaaS offering to allow developers to create add-on applications.
2. Point out the correct statement.
a) Mashups are an incredibly useful hybrid Web application
b) SaaS will eventually replace all locally installed software
c) The establishment and proof of identity is a central network function
d) All of the mentioned
View Answer
Explanation: An identity service is one that stores the information associated with a digital entity in a form that can be queried and managed for use in electronic transactions.
3. Which of the following group is dedicated to support technologies that implement enterprise mashups?
a) Open Alliance Apache
b) Open Mashup Alliance
c) Open Tech Alliance
d) None of the mentioned
View Answer
Explanation: This group predicts that the use of mashups will grow by a factor of 10 within just a few years.
4. Which of the following attribute should be unique?
a) identity
b) digital identity
c) mashup
d) all of the mentioned
View Answer
Explanation: A digital identity is those attributes and metadata of an object along with a set of relationships with other objects that makes an object identifiable.
5. Point out the wrong statement.
a) Distributed transaction systems such as internetworks or cloud computing systems magnify the difficulties faced by identity management systems
b) Services that provide digital identity management as a service have been part of internetworked systems from Day One
c) IDaaS Server establishes the identity of a domain as belonging to a set of assigned addresses
d) None of the mentioned
View Answer
Explanation: The name servers that run the various Internet domains are IDaaS servers.
6. __________ authentication requires the outside use of a network security or trust service.
a) SSO
b) Singlefactor
c) Multi Factor
d) All of the mentioned
View Answer
Explanation: More secure authentication requires the use of at least two-factor authentication.
7. ________ is the assignment of a network identity to a specific MAC address that allows systems to be found on networks.
a) Internet Hardware Addresses
b) Ethernet Software Addresses
c) Ethernet Hardware Addresses
d) None of the mentioned
View Answer
Explanation: Network interfaces are identified uniquely by Media Access Control (MAC) addresses, which alternatively are referred to as Ethernet Hardware Addresses.
8. _________ is one of the more expensive and complex areas of network computing.
a) Multi-Factor Authentication
b) Fault tolerance
c) Identity protection
d) All of the mentioned
View Answer
Explanation: Ticket or token providing services, certificate servers, and other trust mechanisms all provide identity services that can be pushed out of private networks and into the cloud.
9. Which of the following is provided by Identity as a Service?
a) Identity governance
b) Provisioning
c) Risk and event monitoring
d) All of the mentioned
View Answer
Explanation: Identity as a Service or the related hosted (managed) identity services may be the most valuable and cost effective distributed service types you can subscribe to.
10. Which of the following figure fully represent standards needed by IDaaS applications for interoperability?
a)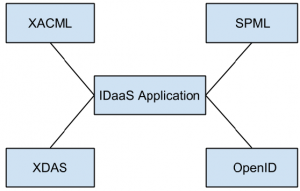
b) 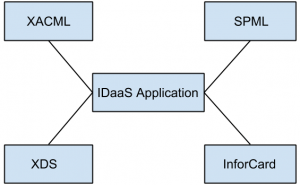
c)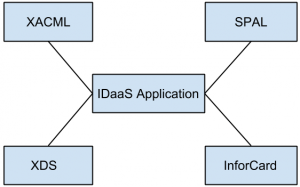
d) 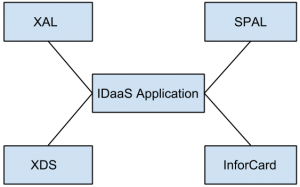
View Answer
Explanation: Cloud computing IDaaS applications must rely on a set of developing industry standards to provide interoperability.
Sanfoundry Global Education & Learning Series – Cloud Computing.
Here’s the list of Best Books in Cloud Computing.
To practice all IDaaS Interview questions, Here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
- Practice Information Science MCQs
- Apply for Computer Science Internship
- Check Computer Science Books
- Practice MCA MCQs
- Check Cloud Computing Books
