This set of Cryptography Multiple Choice Questions & Answers (MCQs) focuses on “Message Authentication Codes (MACs)”.
1. Which figure implements confidentiality and authentication?
a)
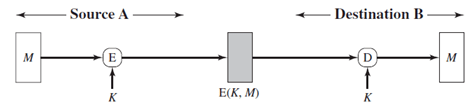
b)
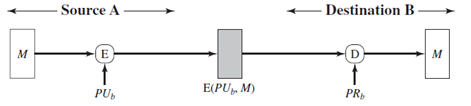
c)
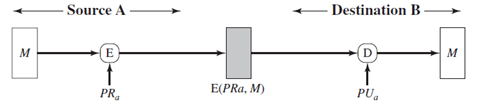
d)
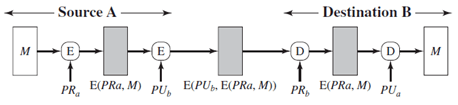
View Answer
Explanation: Figure implements both confidentiality and authentication.
2. Which figure implements confidentiality, authentication and signature?
a)

b)

c)

d)

View Answer
Explanation: Figure implements confidentiality, authentication, and signature.
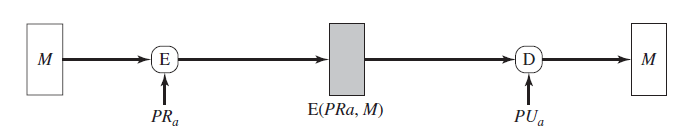
3. The above figure implements authentication and signature only?
a) True
b) False
View Answer
Explanation: The system does not implement confidentiality.
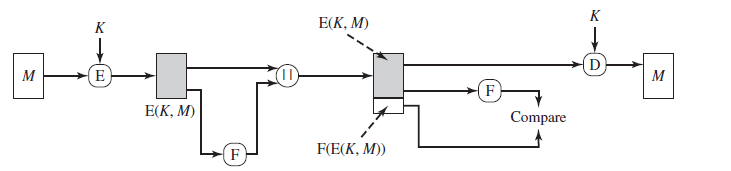
4. The above figure represents internal error control.
a) True
b) False
View Answer
Explanation: The system is that of external error control.
5. Another name for Message authentication codes is
a) cryptographic codebreak
b) cryptographic codesum
c) cryptographic checksum
d) cryptographic checkbreak
View Answer
Explanation: Cryptographic checksum is another name for MACs.
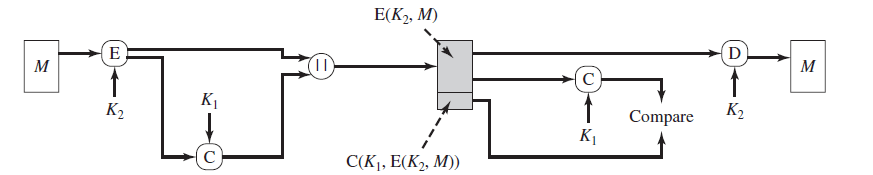
6. The following figure has authentication tied to the plaintext-
a) True
b) False
View Answer
Explanation: The figure has authentication tied to the ciphertext.
7. For a 150-bit message and a 10-bit MAC, how many values are the MAC value dependent on?
a) 2140
b) 2150
c) 215
d) 210
View Answer
Explanation: 2150/210 = 2140.
8. Confidentiality can only be provided if we perform message encryption before the MAC generation.
a) True
b) False
View Answer
Explanation: Confidentiality can be provided even if we perform message encryption after the MAC generation.
9. MACs are also called
a) testword
b) checkword
c) testbits
d) none of the mentioned
View Answer
Explanation: Another term for MACs are tags(or check sum).
10. For a 100 bit key and a 32 bit tag, how many possible keys can be produced in the 3rd round?
a) 24
b) 232
c) 216
d) 264
View Answer
Explanation: First round: 100 – 32 = 68
Second round: 68 – 32 = 36.
Third round: 36 – 32 = 4.
Therefore 24 keys can be produced by the third round.
11. MAC is a
a) one-to-one mapping
b) many-to-one mapping
c) onto mapping
d) none of the mentioned
View Answer
Explanation: MACs are many to one mapping, which makes it tougher for the intruder for cryptanalysis.
12. For an n-bit tag and a k-bit key, the level of effort required for brute force attack on a MAC algorithm is
a) 2k
b) 2n
c) min(2k,2n)
d) 2k/2n
View Answer
Explanation: The level of effort required for brute force attack on a MAC algorithm is min(2k,2n).
Sanfoundry Global Education & Learning Series – Cryptography and Network Security.
To practice all areas of Cryptography and Network Security, here is complete set of 1000+ Multiple Choice Questions and Answers.
If you find a mistake in question / option / answer, kindly take a screenshot and email to [email protected]
- Practice Computer Science MCQs
- Check Computer Science Books
- Apply for Computer Science Internship
- Check Cryptography and Network Security Books
- Practice Cyber Security MCQ
